More and more organizations are building applications in the public cloud. Cloud service providers such as Amazon Web Services (AWS) are making it easier to build and scale applications on-demand. Cloud platforms such as AWS, have established security programs and certifications organizations can utilize to jump-start their security and compliance efforts.
While building cloud applications enables teams to avoid dealing with physical infrastructure, the tasks of building around security, high availability are still present. DevOps processes are becoming an increasingly more important part of the security process.
Setting Cloud Security Standards
Setting predictable cloud security standards and security configuration is becoming more important. With a single Amazon S3 configuration issue resulting in the latest cybersecurity breach with Capital One, the ramifications for not securing cloud resources can be huge.
Organizations must take steps for managing cloud configuration and security operations. Below is an overview for how organizations can start building cloud security controls.
Implement configuration management processes:
Organizations should create a predictable process for building and deploying applications. When operating systems, software, and infrastructure are setup manually, services may be fragile and security issues may occur as the result of human error. Development teams should treat applications and services as disposable and replaceable. Teams may consider using configuration management tools such as Chef, Puppet, and Ansible, as well as orchestration tools such as Terraform and CloudFormation.
Develop standard operating procedures (SOPs) for creating cloud resources:
AWS provides a many options for security configuration with cloud services, but it is the organization’s responsibility to implement necessary security controls for each individual AWS service. In other words, it is possible to build on AWS services and not be secure or compliant.
Security configuration can vary across different services (Amazon EC2 security settings differ from RDS security settings), nonetheless teams should implement the following security standards for every AWS resource:
Encryption (at-rest and in-transit) – Utilize encrypted volumes and SSL/TLS for transmitting data across the web. Individual AWS services have different options for encryption and SSL settings.
Access control – Develop necessary permissions sets, and follow the principle of least privilege (POLP), and restrict production access to only necessary staff. AWS IAM allows organizations to set users, roles, and permissions across most AWS services.
Firewall/networking configuration – Restrict network configuration to only necessary ports and services. Teams can turn to AWS Security Groups or other commercial offerings provide networking options for Amazon EC2 and other cloud services.
Backup and disaster recovery – Create a backup lifecycle for production data on services such as EBS volumes and S3 buckets. Teams should test that backups should be recovered.
Audit logging – Collect system logs, access logs, and error logs across systems and cloud services. Amazon CloudWatch allows organizations to aggregate many types of logs. Additionally, many AWS services can have options for enabling collection of access logs.
Intrusion detection and vulnerability scanning – Scan for vulnerabilities across your systems and implement a patching schedule. Use intrusion detection tools to monitor and avoid malicious behavior.
Set and maintain security controls using Dash
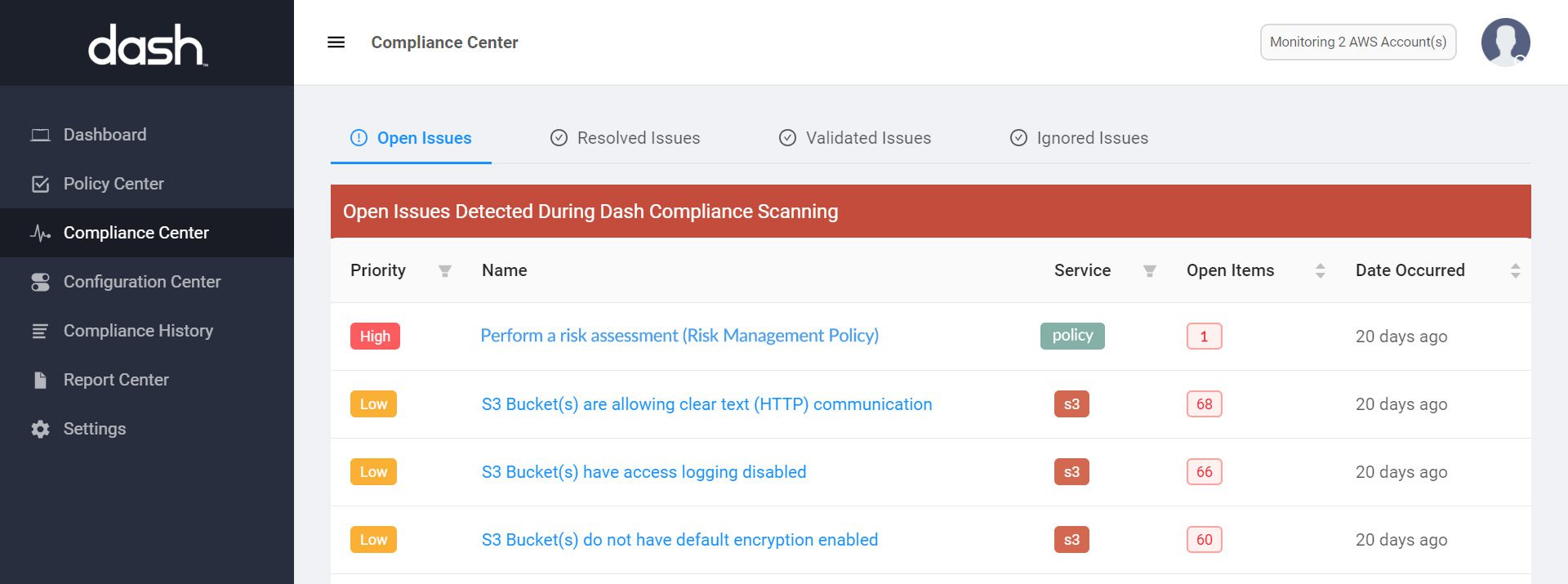
Dash can help organizations set cloud security controls and automatically monitor cloud configuration. Organizations can set baseline cloud security controls through policies and set cloud controls:
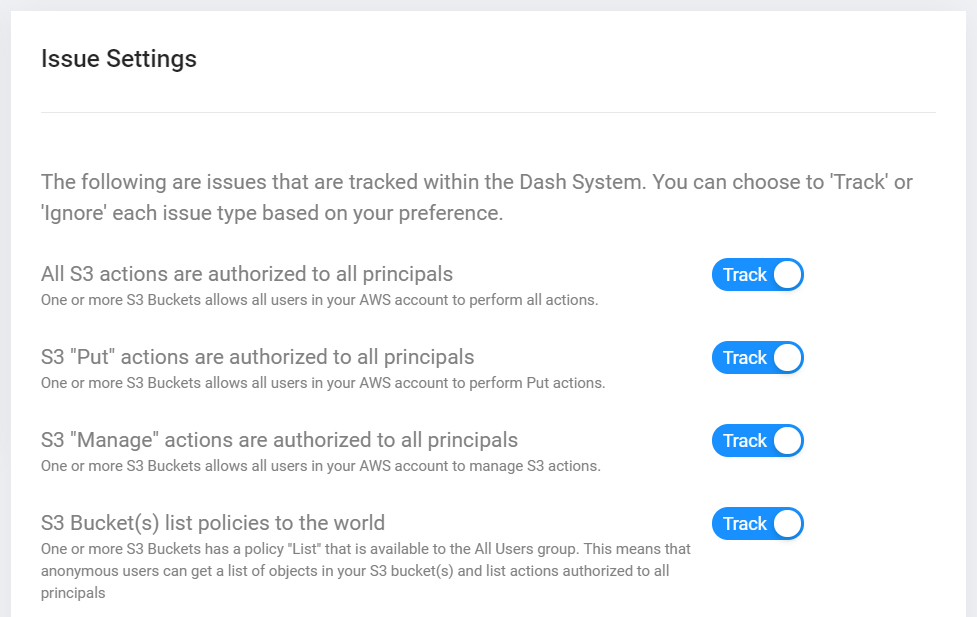
After setting cloud security policies and controls Dash will automatically detect security issues throughout the AWS environment using Continuous Compliance Monitoring. Teams can identify cloud security issues such as “Unencrypted EBS volumes”, “Publicly available S3 buckets” and resolve these issues. Issues are mapped to cybersecurity frameworks and regulatory requirements including HIPAA/HITECH, NIST CSF, etc.
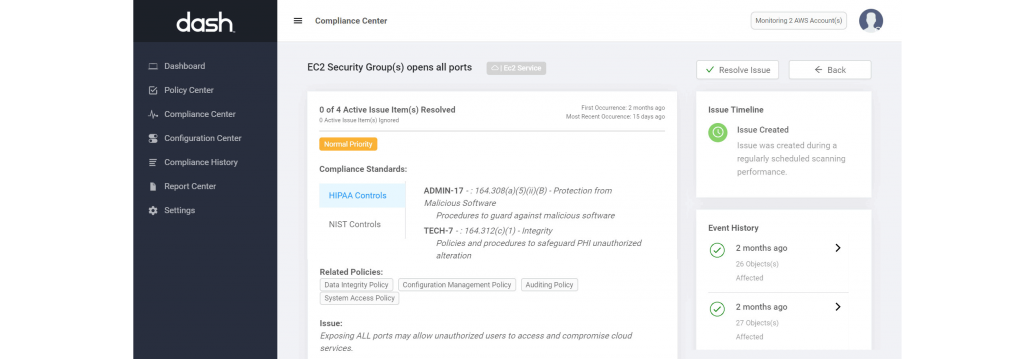
Proactively Addressing Security and Compliance Issues
After configuring cloud security standards and creating secure resources, teams must continue to monitor for further cloud security issues. As organizations continue to scale and applications grow, new cloud resources are created. Organizations must account for “operational drift”, meaning that current new organizational practices may not reflected in policy, or AWS configuration may fall out of compliance with security standards.
“Organizations building secure applications in the cloud must account for operational drift, the concept that cloud resources may fall out of compliance with security standards as organizations grow, security policies are modified, and applications change.”
Teams should consider taking the following steps for proactively addressing security concerns in the cloud:
Create Security Alerts
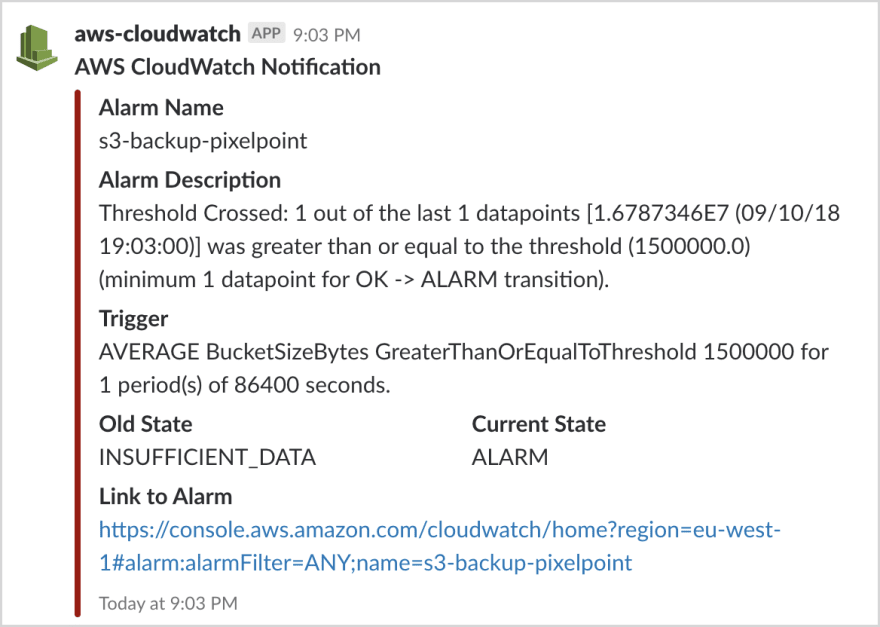
DevOps staff should be monitor cloud environments for potential security and configuration issues. Teams may consider connecting cloud services such as Amazon CloudWatch to Lambda and SNS to send security configuration and availability alerts via email and Slack alerts.
Alex Barashkov from Pixel Point shared a great tutorial for connecting CloudWatch Alarms to Slack.
Enable Dash Security Compliance Alerts
Dash provides teams with the ability to monitor cloud security and compliance for all AWS resources. Organizations can enable email and Slack notifications for cloud security and compliance issues. Dash provides organizations with all compliance issues. Security team members can use Dash automatic remediation and “click-to-fix” to resolve cloud security issues with one click.